
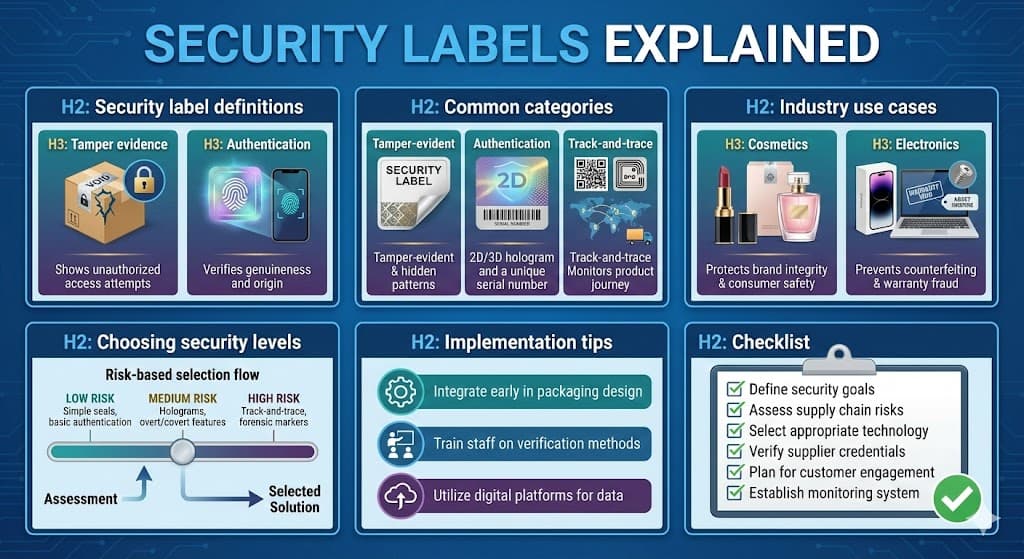
Modern brand protection relies heavily on the physical layer of packaging security. Security labels serve as the primary interface between a product and the consumer or inspector. They are no longer simple stickers but complex engineering feats designed to defend against sophisticated counterfeiting rings.
The efficacy of a security strategy depends on the seamless integration of material science and data management. Brands must move beyond aesthetic considerations to evaluate the functional resilience of their labeling solutions. This ensures that the physical tag acts as a robust barrier against illicit trade and gray market diversion.
Supply chain integrity demands a multi-layered approach to asset tagging. A single layer of protection is rarely sufficient in the current global marketplace. Effective labeling combines overt elements for quick visual verification with covert features for forensic analysis and legal enforcement.
Security labels are functional components engineered to validate authenticity or indicate interference. They utilize specialized substrates, proprietary adhesives, and advanced printing techniques. Unlike standard packaging labels, their primary function is risk mitigation rather than mere information delivery or branding.
These labels function as a lock on the product packaging. The complexity of the lock depends on the value of the goods and the capability of the threat actors. High-performance labels incorporate features that are difficult to replicate using standard darker market printing equipment.
Substrates play a critical role in the definition of a security label. Materials such as ultra-destructible vinyl or frangible paper effectively prevent label removal. If an attempt is made to peel the label, the material fractures into tiny pieces, rendering the label useless for reuse on fake products.
Adhesive chemistry is equally important in this definition. Security adhesives are formulated to bond aggressively to specific surface energies. Whether applied to coated cardboard, glass, or plastic, the bond must be stronger than the face stock material itself to ensure structural failure upon removal attempts.
The printing technology defines the third layer of a security label. Variable data printing allows for unique serialization, giving every single unit a distinct identity. High-resolution micro-text and guilloche patterns add barriers that standard digital copiers cannot reproduce with sufficient clarity.
It is vital to distinguish between tamper evidence and authentication as they solve different problems. Tamper-evident seals answer the question of integrity. They communicate whether the package has been opened, altered, or compromised since it left the manufacturing facility.
Tamper evidence relies on physical destruction mechanisms. Common examples include void pantographs that leave a "VOID" or "OPENED" message on the packaging surface. This residue alerts the consumer or retailer that the product is no longer pristine, protecting against contamination or part swapping.
Authentication focuses on legitimacy and provenance. These features answer the question of origin. An authentication label proves that the item was manufactured by the authorized brand owner. A package can remain perfectly sealed (intact integrity) yet still be a total counterfeit.
Authentication utilizes technologies like holograms, optically variable devices (OVDs), and taggants. These features are difficult to forge. While a tamper seal protects the contents, the authentication feature protects the intellectual property and the brand reputation itself.
combining these two functions creates the most robust defense. A label that verifies origin through a hologram and simultaneously destroys itself upon removal prevents a genuine label from being harvested and placed on a fake product. This dual-functionality is the industry standard for high-risk goods.
Protective labeling is categorized by the method of verification and the technology employed. The primary division lies between overt and covert technologies. Overt features are visible to the naked eye and intended for immediate validation by consumers without special tools.
Holograms and color-shifting inks fall into the overt category. These optically variable features change appearance based on the viewing angle. They provide an intuitive verification method but can sometimes be simulated by advanced counterfeiters, requiring frequent design updates.
Covert categories include features hidden from normal view. UV-luminescent inks, which only appear under black light, are standard covert tools. These allow customs officials and field investigators to verify products discreetly without alerting the suspect or relying on consumer knowledge.
Forensic markers represent the highest category of security. These utilize molecular taggants or DNA markers embedded in the ink or substrate. Detecting these requires laboratory equipment or proprietary handheld scanners, providing evidence admissible in court for legal action against counterfeiters.
Another category involves destructible substrates used specifically for warranty enforcement. These labels are often made of acetate or fragile vinyl. They prevent consumers from opening electronics to swap internal components while claiming the device is original and unopened.
Track-and-trace converts a static label into a dynamic digital asset. This category focuses on supply chain visibility rather than just physical verification. By assigning a unique serial number or UID to each label, brands can monitor the movement of unit-level items globally.
QR codes and Data Matrix codes are the standard vehicles for this data. When scanned, these 2D barcodes connect to a cloud database. This connection allows for real-time authentication and provides data on where the scan took place, helping identify unauthorized diversion routes.
RFID (Radio Frequency Identification) and NFC (Near Field Communication) represent the premium tier of track-and-trace. These inlays allow for non-line-of-sight scanning. Implementing RFID enables rapid inventory management and automated shipping verification, drastically reducing human error in the supply chain.
Serialization software prevents code duplication. sophisticated algorithms generate random, non-sequential numbers that are impossible to guess. If a counterfeiter copies a valid QR code, the system flags the anomaly when the same code is scanned in two different geographic locations simultaneously.
This digital layer aids in combating gray market diversion. If a product designated for a specific market receives a scan in a prohibited region, the brand owner is alerted. The label becomes a tool for enforcing distribution agreements and maintaining global pricing structures.
The application of security labels varies significantly across industries based on regulatory requirements and risk profiles. The pharmaceutical industry operates under strict serialization mandates. Labels here must ensure patient safety and comply with regulations like the Falsified Medicines Directive or DSCSA.
Automotive parts manufacturers utilize security labels to ensure vehicle safety. Counterfeit brake pads or airbags pose lethal risks. Labels in this sector must withstand extreme environments, including high heat, grease, and hydraulic fluids, without losing adhesion or legibility.
The spirit and wine industry faces high risks of refilling fraud. High-value bottles are often retrieved from trash, refilled with cheap alcohol, and resealed. Security tax stamps and capsule seals that break upon opening are essential to prevent this type of revenue loss.
Agrochemicals employ security labels to protect crop yields. Fake fertilizers and pesticides can destroy harvests. Labels in this sector often use multi-page booklets containing safety data, integrated with overt authentication features to reassure farmers of the chemical's potency and origin.
Cosmetics and personal care high-value items require a balance of security and aesthetics. The packaging is a major part of the consumer experience. Security labels must not detract from the brand image or leave sticky residue that ruins the premium feel of the container.
Diversion is a massive issue in cosmetics. Distributors often sell professional-grade products on unauthorized online marketplaces. Coding on labels helps brands conduct test buys to identify the rogue distributor. Often, these labels use transparent substrates to blend seamlessly with the package design.
Electronics rely heavily on warranty void labels. These are placed over screw holes or chassis seams. The primary goal is to prevent the harvesting of genuine internal parts or the return of goods that have been tampered with by third-party repair shops.
Use cases in electronics also involve component authentication. Batteries and chargers are frequent targets for counterfeiting, posing fire risks. Holographic labels on battery packs provide a quick visual check for consumers to ensure they are using safe, OEM-certified power sources.
Both sectors benefit from near-field communication (NFC) labels. In cosmetics, an NFC tap can provide product tutorials, adding value while verifying authenticity. In electronics, NFC can register the device for warranty instantly, linking the physical hardware to the user’s digital profile.
Choosing the right security level requires a comprehensive risk assessment. Brands must calculate the cost of doing nothing versus the cost of implementation. If the potential revenue loss or liability from counterfeits exceeds the investment in labels, high-level security is justified.
Analyze the sophistication of the threat. If the counterfeiters are using advanced printing presses, a simple hologram is insufficient. In such cases, a combination of OVDs and forensic taggants is necessary to stay ahead of the technical capabilities of the criminal enterprise.
Consider the product lifespan and value. Low-value, fast-moving consumer goods may only require simple tamper-evident tape. High-value durable goods require permanent, serialized authentication labels that remain legible for years.
Evaluate the checking environment. Who is verifying the label? If consumers are the primary inspectors, overt features like color-shifting ink are best. Is the product checked by customs officers? Then covert UV features or handheld scanner-readable codes are required.
Think about the "arms race" aspect of security. Static security features eventually get compromised. The chosen solution should allow for periodic design refreshes or technology upgrades without requiring a complete overhaul of the packaging production line.
Successful implementation starts with the application surface. The substrate of the packaging dictates the adhesive choice. A label designed for a cardboard box may fall off a textured plastic surface. Testing adhesion on the actual production packaging is a non-negotiable step.
Application temperature and environmental conditions matter. Labels applied in freezing warehouses require different adhesives than those applied in humid tropical facilities. Failure to account for these variables results in premature label failure and compromised security.
Automated application speeds must be considered. High-speed production lines require release liners that can withstand tension without tearing. The security cuts in a destructible label must be engineered so the label doesn't break during the machine dispensing process.
Employee and stakeholder training is critical. A security feature provides no value if the people handling the product do not know how to validate it. Retailers, distributors, and consumers need clear instructions on what to look for and how to interpret the label’s visual cues.
Software integration must be robust. If using track-and-trace, the serialization data must sync flawlessly with the ERP system. There should be a defined protocol for what happens when a fake code is detected, including automated alerts to the brand protection team.
Define the primary goal clearly. Determine if the priority is anti-counterfeiting, anti-diversion, or tamper evidence. Mixing up these priorities can lead to purchasing the wrong technology for the specific threat facing the brand.
Select the appropriate substrate and adhesive. Ensure the material will destruct upon removal and stick permanently to the product surface. Conduct aging tests to ensure the adhesive does not dry out or fail over the shelf life of the product.
Layer the security technologies. Combine at least one overt feature for the public with one covert feature for investigators. This creates a balanced defense that is easy to check but hard to copy.
Plan the data management strategy. If using QR codes or serialization, ensure the backend infrastructure is secure. The database holding the valid serial numbers is just as valuable as the physical product and must be protected from cyber threats.
Establish a monitoring program. A label is a tool, not a solution. set up a schedule for market surveys and test buys. Use the intelligence gathered from the labels to take legal action or adjust distribution channels.
Review and update regularly. Security is not a one-time project. Schedule annual reviews of the label technology. Engage with vendors to learn about new substrates or inks that can keep the brand one step ahead of counterfeiters.